This is a complete guide to the ROT13, ROT47 and ROT18 cipher and the tools you need to decode it.
Have you ever been on an internet forum and seen a spoiler that has been encoded into an unreadable message? If you have then the chances are you’ve already come across ROT13. It’s a cipher that is commonly used for disguising non-sensitive information such as puzzle solutions or NSFW (not suitable for work) messages. But this code has its roots all the way back in Roman history.
ROT13/ROT47/ROT18 Tool
Explanation
| Letter | Translation |
|---|
Options
Text processing
What is ROT13?
ROT13 is a shift cipher, that’s a simple kind of encryption where the ciphertext is created by taking the plain text message and shifting (moving forward in the alphabet) by a certain number of letters. The name is a shorthand version of ‘rotation 13’. It’s also a type of substitution cipher, because one letter is substituted for another.
What makes ROT13 unique is that it is its own inverse. Because the alphabet is 26 letters, and the shift is 13 letters, A translates to N and vice versa. However, it doesn’t encode numbers or punctuation, which gives it some limitations.
Decoding ROT13
ROT13 is easy to translate without any tools. If you think might be looking at a piece of ROT13 code, all you need to do is to write the letters A-M on a piece of paper, and the letters N to Z below them. You can then substitute the letters accordingly, so if the cipher text has a letter A, the plain text is N and vice versa.
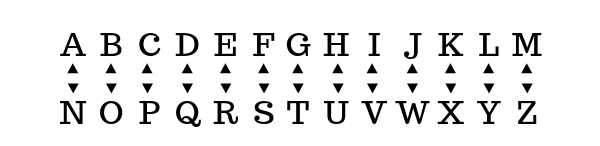
For example, HELLO, would be translated to URYYB:

If you come across some code and you’re not sure if you are looking at ROT13 or another, similar cipher you can use frequency analysis to identify the shift. Find the most commonly used character in the cipher text. The most commonly used letter in English is the letter E, so if your most frequently used character is R, you’re probably looking at ROT13.
History
Shift ciphers are also known as Caesar Ciphers. That’s because the first recorded case of the shift cipher being used was by Julius Caesar. In his private correspondence, Julius Caesar would use a 3-letter shift to make his messages more difficult for prying eyes to read. ROT13 itself is much more modern. It rose to prominence in the 1980’s when it was used in the net.jokes newsgroup in the early days of the internet. It was used then to hide offensive jokes, letting a person choose if they wanted to view the content or not. It went on to become a simple way to hide the solution to online puzzle games and was often described as the encryption equivalent of turning a piece of paper upside down to read the answers. The treasure hunting website, Geocaching.com, uses encrypted hints to the locations of geocaches using ROT13. Although ROT13 is not a secure cipher, it has been used in some commercial applications. In 1999 it was discovered that Netscape Communicator was using the cipher to encrypt passwords. Two years later, the eBook vendor NPRG were revealed to be using ROT13 to encrypt their content. These aren’t the only examples, though. Windows XP used ROT13 to encrypt registry entries. The UNIX fortune program also used the cipher to hide potentially offensive material.
Current Usage of ROT13
Because there is no key needed to encrypt ROT13, it’s not used for serious commercial purposes. In fact, ROT13 has become something of a joke in terms of its effectiveness. It’s not uncommon to hear security experts deride insecure solutions by saying, ‘That’s about as much use as ROT13!’
On a similar note, you may hear techies talking about ROT26 or double ROT13/2ROT13. ‘It’s like ROT13, but twice as secure!’ If you don’t get why this is a joke, think about writing the letters A-Z on the top row, and again on the bottom. In other words, this sentence is already encrypted in ROT26. Congratulations on cracking the code.
ROT13 does still have its uses, however. It continues to be used to hide spoilers or NSFW content on forums and the like. It’s also used to encode email addresses, to keep them from the grips of the spam bots.
As a mental exercise, ROT13 can be used for letter games. You can look for words which, when encrypted, spell out other valid words. Examples of these are Gnat and Tang, and Abjurer/Nowhere.
Perhaps the most extreme version of this wordplay is Brian Westley’s entry to the 1989 International Obfuscated C Code Contest. Brian wrote a piece of C code which would compile either as written, or when encrypted using ROT13. The icing on the cake is that the code itself encrypts and decrypts ROT13.
If you’ve ever been in a newgroup or internet forum and seen users exclaim, ‘Fuurfu!’ then you’ve been reading ROT13. This all started when someone claimed the word, ‘Sheesh!’ was being overused. This led to some wise cracker using ROT13 to encrypt the exclamation, and the idea caught on.
Variants
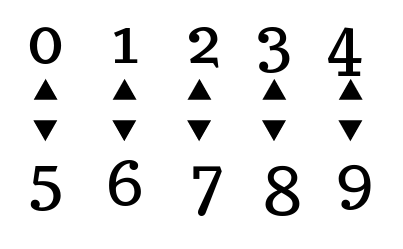
ROT5 is the numeric equivalent of ROT13. The numbers 0-4 are written on the top row, and 5-9 on the bottom. This allows numbers to be encrypted in the same manner as ROT13, by using their inverse. Using ROT13 and ROT5 together is sometimes called ROT18.
Another alternative is ROT47, which uses a similar principle but encrypts all the visible ASCII characters allowing letters, numbers and punctuation to be encoded. It uses ASCII characters 33-126, which covers most of the characters available on a QWERTY keyboard.
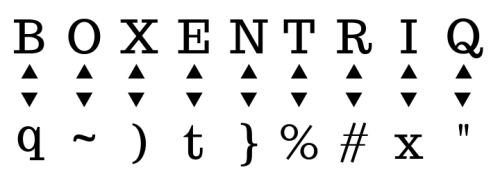
Shifting the Cipher
While it should never be used for serious encryption, ROT13 still has a lot to offer. Because it has no key, it allows you to share encrypted text with others who can then easily decipher them making it useful for hiding information such as hints or spoilers until the reader is ready to see them.
It’s useful in puzzles, as no special equipment is needed to decrypt it. A pencil, paper and a little bit of patience is all that’s needed to crack this code, or any of the other Caesar ciphers. Why not try this puzzle?
nyy lbh unir gb qb vf gb xabpx gur urryf gbtrgure guerr gvzrf naq pbzznaq gur fubrf gb pneel lbh jurerire lbh jvfu gb tb
See also: Code-Breaking tools | Adfgvx cipher | Adfgx cipher | Affine cipher | Atbash cipher | Baconian cipher | Beaufort cipher | Bifid cipher | Caesar cipher | Columnar transposition | Cryptogram | Double transposition | Enigma machine | Four-square cipher | Gronsfeld cipher | Keyed caesar cipher | One-time pad | Pigpen cipher | Playfair cipher | Rail fence cipher | Route transposition | Substitution cipher | Trifid cipher | Variant beaufort cipher | Vigenere cipher